Automate Your Zero Trust Networking Solution
Mani Subramanian
on
8 4 月, 2022


I’m noticing a lot more traffic on Silicon Valley freeways. Are you ready to go back to the office now? Campuses are now welcoming back workers, and this means that Access Switches need to support more users, IoT and other devices and guests. Pica8 software helps automate your Zero Trust Networking solutions to get your organization working safely and efficiently.
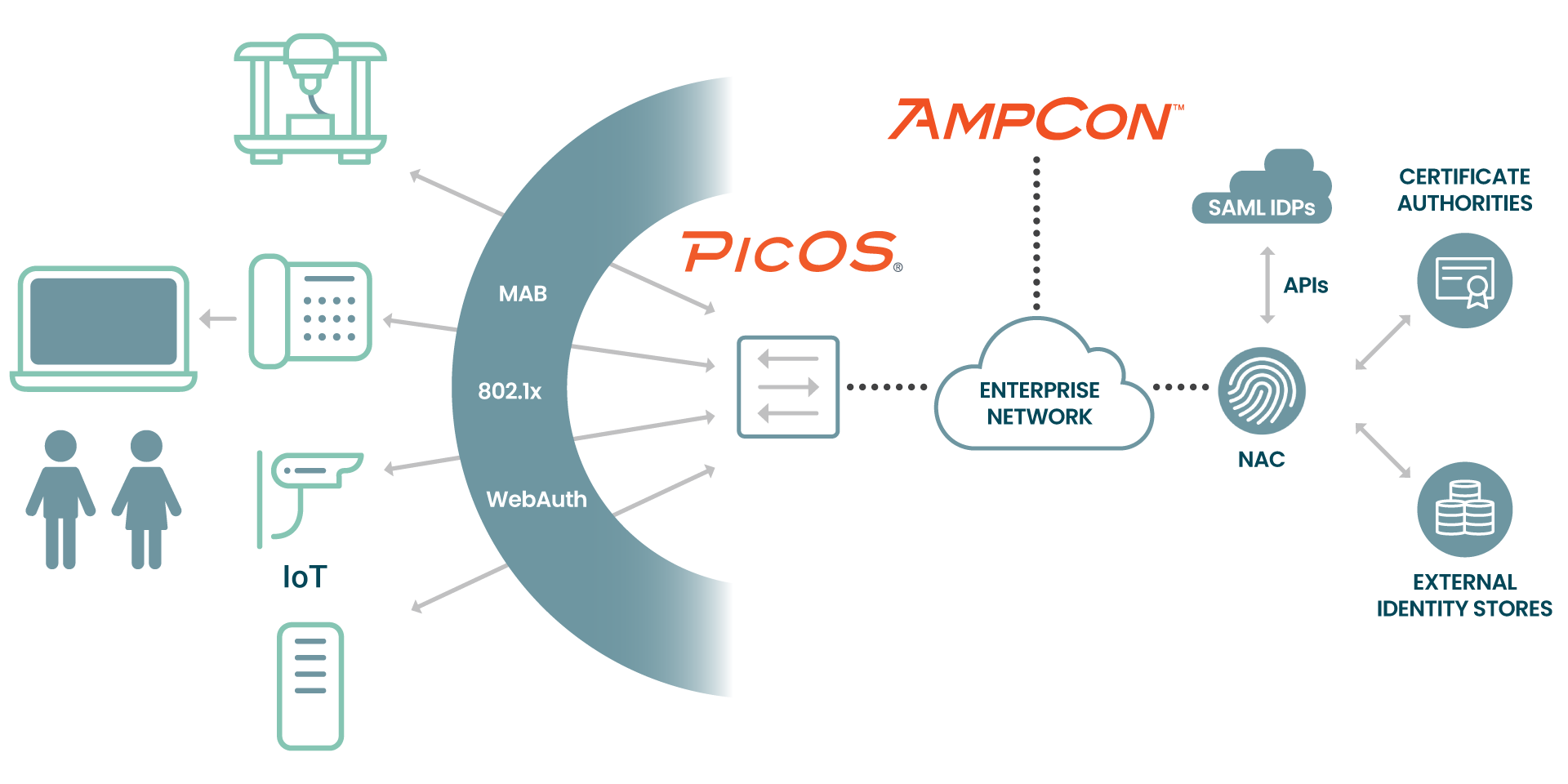
 This blog covers features supported, best practice configuration and automation of the Pica8 Secured Wired Network Access Controller (NAC) Solution. Users and endpoints in the Campus or Data Center are not trusted until they are authenticated using Zero Trust Networking through NAC integration with major RADIUS server products. Following is the topology of our Secured Wired Access Solution. User devices and endpoints are connected to Pica8’s PicOS software on Access Layer PoE switches. In this use case the RADIUS server in the enterprise authenticates the users and endpoints.
This blog covers features supported, best practice configuration and automation of the Pica8 Secured Wired Network Access Controller (NAC) Solution. Users and endpoints in the Campus or Data Center are not trusted until they are authenticated using Zero Trust Networking through NAC integration with major RADIUS server products. Following is the topology of our Secured Wired Access Solution. User devices and endpoints are connected to Pica8’s PicOS software on Access Layer PoE switches. In this use case the RADIUS server in the enterprise authenticates the users and endpoints.
Our AmpCon Network Controller automates your configuration, policies and deployment including zero touch provisioning. Our PicOS software turns your white box into an enterprise networking switch with fully integrated NAC solutions for Zero Trust Networking.
This blog helps you to reduce deployment time significantly for Zero Trust Networking solutions by providing the following:
- Best practice NAC configurations for PicOS in a nutshell
- Automate and verify NAC configurations for Access Switches
- How to integrate and test with popular RADIUS servers in the market
PicOS Network Access Control: Zero Trust Networking Solution Overview
PicOS supports the following Secured Wired Access solutions:
- Authentication Methods: Following authentication methods are supported.
- 802.1x
- MAC Authentication Bypass (MAB or MAC-RADIUS)
- Central Web Authentication (CWA)
- Multi-host support: Support for multiple endpoints to be connected to the network through the same switchport
- Policy Enforcement: The following network policies can be enforced
- Dynamic VLAN Assignment (by ID and Name)
- Dynamic Access Control List (ACL)
- Downloadable ACL
- CoA (Change of Authorization)
- Server Fail VLAN: Provide limited network connectivity to users in the event of AAA server failure
Pica8’s Secured Wired Access solution consists of authenticating the following use cases:
- User Based Authentication: Employee laptops will have 802.1x supplicant. We will use 802.1x authentication for Employees.
- Device Based Authentication: We will use MAB (MAC Address Bypass) Authentication for authenticating devices. Following are example use cases for authenticating devices:
- Group of IP Phones
- Group of IoT Devices
- Contractor laptops are authenticated using MAB and Central Web Authentication
- Multi-host Authentication: This case includes more than one device connected to a switch port. Following is one example use case: Employee laptop connected behind an IP Phone and IP Phone is connected to the switch.
RADIUS server is configured with the following Secured Access Policies. Once the user or device is authenticated using RADIUS server, the following secured access techniques are assigned to the port as per Policy settings in the RADIUS server.
- Dynamic VLAN
- Either Dynamic or Downloadable ACL
Automate NAC Configuration
For best practice PicOS NAC configurations and info on how to automate NAC configuration for Access Switches, please refer to our Tech Note.
Integration With Popular RADIUS Servers
PicOS integrates with popular RADIUS servers. Please refer to the following documents to save deployment time.
- PicOS NAC Integration with Cisco Identity Service Engine (ISE)
- PicOS NAC Integration with Aruba ClearPass Policy
Conclusion
Pica8 automates Zero Trust Networking with our All-in-One Enterprise Software Suite, which includes our AmpCon Network Controller and PicOS software. Our software will save you hours by automating your Zero Trust Networking solution.
Contact us today to learn more about PicOS, AmpCon and Zero Trust Networking automation.
—-

Mani Subramanian is Senior Technical Marketing Manager for Pica8
- Category: Uncategorized
- Tag: automation, network configuration
