Tech Blog: Network Access Control with Open Campus Networks
Mani Subramanian
on
1 10 月, 2020

Years ago, Network Access Control (NAC) was a high-end security feature touted by legacy network switch vendors. But like so many other legacy vendor features, NAC has been successfully adopted by open network vendors and is ready for deployment in enterprise campus and access networks as part of a more modern architecture.
NAC is a security solution that enforces policy on devices as they seek access to a network to increase network visibility and reduce risk. For example, NAC may be used to ensure anti-virus software is up to date and, if not, ensure that it’s updated before the device is granted network access. It can also be used to define what resources a given device can access, as well as what VLAN and what ACL should be applied to it. NAC integration is now becoming increasingly important to the network security of enterprises.
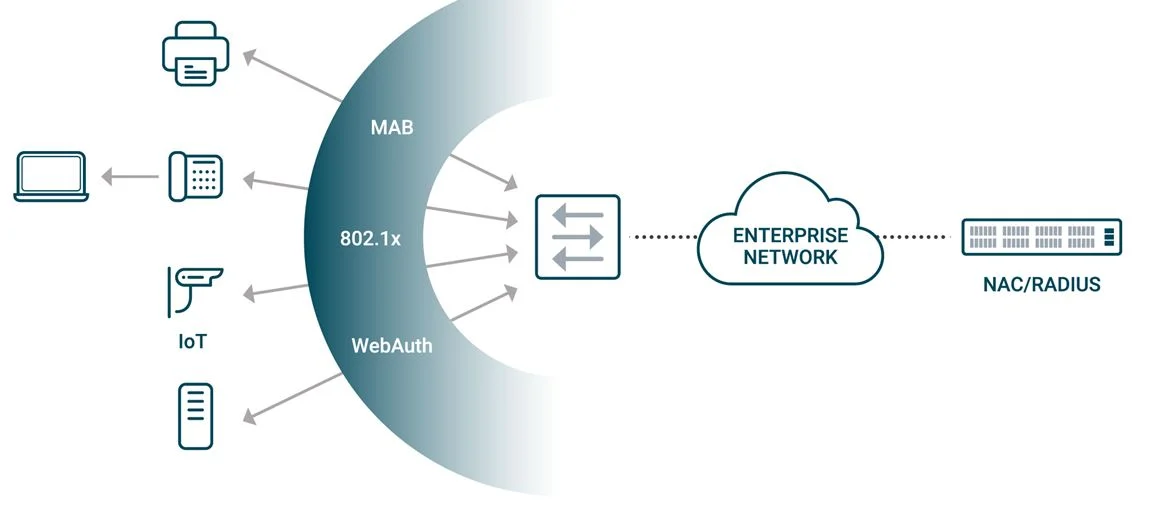
From a high-level point of view, NAC is a typical SDN application, one that leverages a centralized controller to control the network access authentication and authorization of many switches. The NAC controller authenticates the devices accessing the network and sends instructions to the switches, which apply different policies to the end devices.
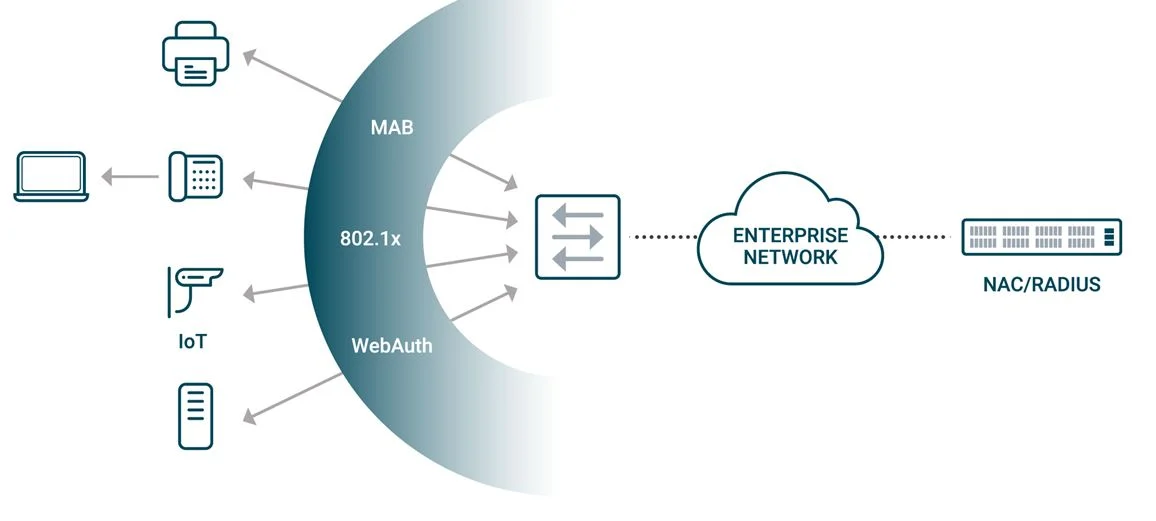
Typically, a NAC controller consists of an integrated identity database and certificate process. It communicates with switches through 802.1x, MAC Address Bypass (MAB) and Web authentication (WebAuth) protocols. The switches need to support 802.1x, Voice VLAN, MAB, WebAuth, and Dynamic/Downloadable ACL policies.
Most new NAC users start by choosing a NAC controller, such as Cisco ISE or Aruba ClearPass. Organizations need to think through their security requirements and make decisions on the operation models, such as:
• Whether policies are applied pre-admission or post-admission
• Agent or agentless
• Out-of-band or inline
• Remediation, quarantine and captive portals
Plenty of resources are available on the internet to compare the advantages and disadvantages of various NAC controllers. For more details, we recommend users start with the NAC entry on Wikipedia.
In this blog, we focus on the NAC support at the switch side. While 802.1x is an open standard, NAC is much more than just 802.1x. From the perspective of qualifying the NAC support of switches, users need to consider the following factors:
• 802.1x, Mac Address Bypass (MAB) and Web Authentication (WebAuth)
• Dynamic VLAN
• Dynamic ACL and Downloadable ACL
• Integration with the NAC Controllers
• Multiple NAC controllers
• Troubleshooting tools
Mac Address Bypass (MAB) and Web Authentication (WebAuth)
While 802.1x is an open standard, not all devices support 802.1x authentication. When some devices do not support 802.1x, the NAC solution usually needs to integrate MAB and WebAuth as the fallback operation. In this case, MAB works by having the switch send the MAC address of the “authenticating” device to the NAC controller, which then checks its policy to decide whether to grant or reject the access request. On the other hand, WebAuth allows the devices to connect to a web portal for authentication.
No matter if a device is authenticated through 802.1x, MAB or WebAuth; after the authentication, the connected switch will apply any dynamic policies provided by the NAC controller on the newly authenticated device.
Pica8’s PICOS open network operating system provides a flexible way for users to set which authentication methods to use on a per-port basis. For example, if users want port 1/1/9 to utilize 802.1x, MAB and WebAuth:
set protocols dot1x interface ge-1/1/9 auth-mode 802.1x
set protocols dot1x interface ge-1/1/9 auth-mode mac-radius
set protocols dot1x aaa web server-ip 10.10.50.65
set protocols dot1x interface ge-1/1/9 auth-mode web
However, in case users want to use only 802.1x, and MAB:
set protocols dot1x interface ge-1/1/9 auth-mode 802.1x
set protocols dot1x interface ge-1/1/9 auth-mode mac-radius
Dynamic ACL and Downloadable ACL
Even though the main purpose of NAC is to authenticate end devices to access the network, most NAC implementations can do more than just authentication. One major feature of NAC, for example, is to apply ACL rules to the newly authenticated session. This can be done through Dynamic ACL or Downloadable ACL.
Basically, a Dynamic ACL is pre-defined on the switches, and NAC servers simply send the ACL name to the switches, which apply them to the new session. A downloadable ACL, on the other hand, is defined on the Radius server, and the NAC controller sends that ACL to the switch after a session is authenticated.
PICOS supports both Dynamic ACL and Downloadable ACL. This maximizes the compatibility between PICOS and commercial NAC vendors, and also gives users flexibility in defining security policies.
Integration with the NAC Controller
Even though most NAC controllers use 802.1x to communicate with switches, there are always tricky integration details that need to be qualified and resolved before NAC can be deployed into a production environment.
From the integration point of view, PICOS has been qualified and deployed into production with many NAC controllers, including Cisco ISE, Aruba ClearPass, OpenNAC, and PacketFence.
To configure the NAC controller on the PICOS switch, use the following configurations:
set protocols dot1x aaa radius authentication server-ip 10.10.50.65
shared-key “test-key”
set protocols dot1x aaa radius dynamic-author client 10.10.50.65
shared-key “test-key”
set protocols dot1x aaa radius nas-ip 172.16.0.193
Multiple NAC controllers
NAC plays a critical role in controlling network access, which makes high availability an important requirement. To achieve real redundancy, each switch needs to be able to connect to multiple NAC controllers.
Switches running PICOS can connect to up to 3 NAC controllers. Each NAC controller can be configured with a different priority, so network administrators can specify the order in which AAA transactions are sent to NAC servers, based upon their availability. In the failover case, administrators have the option to configure retry numbers, retry intervals, and detect intervals to optimize the fail-over design.
Here is an example of configuring multiple controllers on a PICOS switch:

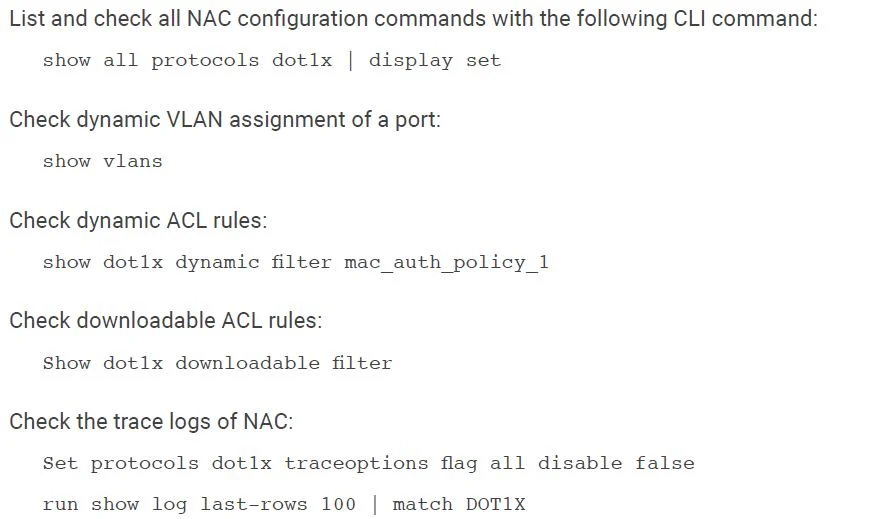
Troubleshooting Tools
NAC is a sophisticated feature and requires several tools for troubleshooting. Besides “show dot1x server”, PICOS also supports the following commands and tools for the operation support:

NAC is Ready for Open Networks
If you’ve been interested in the concept of open networking but not sure whether security solutions like NAC would be available, hopefully this post answers that question. Enterprises and data center operators are rapidly adopting open networking and realizing the many cost and operational benefits it provides. They are finding being open doesn’t mean sacrificing advanced features. NAC is just one example of a feature that used to be available only from high-end legacy network vendors but that is now readily available for open networks.
To learn about many more such features, check out this solution brief on Threshold™, Pica8’s reference architecture for open campus networking.
Mani Subramanian is Senior Solutions Manager for Pica8.
- Category: Uncategorized
- Tag: open networking
